Reports of data breaches occur at greater and greater frequency as digital services continue to dominate the world. These breaches happen across a spectrum of organizations from tech companies to government bureaucracies. An unfathomable amount of personal information and passwords have been exposed, leaving millions of accounts vulnerable.
Since the inception of internet based services, almost all accounts have been secured with a username and password combination. What can we do to mitigate the potential damages of our personal credentials such as username and passwords ending up in the wrong hands?
Two-factor authentication(2FA) is one safeguard against this very real vulnerability.
Two-factor authentication is an extra layer of security that can be added to many of the sensitive accounts a user accesses daily. Sometimes two-factor authentication is required by an application but many times it’s optional. After entering your account credentials (the first factor) applications that employ two-factor authentication will then ask for a secondary piece of information that ideally only the user has knowledge of and/or access to. These secondary pieces of information are usually produced by one of four possible solutions: personal knowledge, specialized hardware, biometrics, or software.
Knowledge
The knowledge solution is usually an extra piece of information determined by the user. Many users are familiar with a PIN(Personal Identification Number) when using a debit card. The PIN is an often cited example of a second factor used for authentication. Another knowledge solution might be a user picking a specific question and answer combo as the second factor. These are fairly simple solutions but can be fairly easy to guess by malicious actors. When compared to other solutions knowledge-based second factors can seem pretty flimsy.
Hardware
The hardware solution utilized specialized devices like Yubikey or another key fob solution that shows a one time use code that is synchronized with the application based on an agreed upon secret key. This is generally a very effective solution and have been around for decades. They are used at large financial corporations throughout the world but the devices can be expensive, have only one use, and are easy to misplace.
Biometric
Biometrics are still pretty advanced for most general applications, but we’re starting to see smartphones and laptops with fingerprint readers or facial recognition. Iris scanning is starting to hit the market now with greater popularity. These can be great in one sense: a malicious actor probably doesn’t have your iris or fingerprint. In another sense, there are very serious concerns about biometrics in general. These concerns are usually general macro concerns that warn of large organizations such as nation-states and multinational technology platforms using biometrics against the populations they are supposed to serve. This is less a specific personal risk than a general social risk.
Software
Software tokens have become the most prevalent adoption of two-factor authentication throughout web applications. SMS or Voice is generally a default used for many sites, because it can be implemented simply through several providers, and allows another identity verification to be added to accounts for applications that need to know their customers. Users are typically sent a one time use code to their phones that act as the second factor. Unfortunately, SMS and Voice are still susceptible to malicious actors through the mobile carriers themselves. Early this year, it was reported, one investor lost over $20k because their T-Mobile account was taken over, and now AT&T is being sued by another investor for $224 million for a similar incident.
There is a safer software token solution available that doesn’t use SMS or voice but instead uses software applications that serve the same function as the hardware solution discussed above. These applications have become very popular, such as Authy or Google Authenticator. These software based solutions work in a similar way to the hardware solution. Applications such as Google Authenticator produce a one-time use code as the second factor. Although the token generation works like the hardware solutions the software token can be backed up and restored to new devices in the situation where the original device is lost. This is not the case with hardware based solutions.
Two-Factor Authentication in Edge
Here at Edge we built a software token solution directly into the Edge Wallet! When setting up two-factor authentication in Edge there is no need for an extra application like Google Authenticator. The Edge Wallet generates a unique token and saves it on the user’s device with just the tap of a button. There is no need for extra knowledge, specialized hardware, biometric information, or an extra application to download when setting up and using Edge’s 2FA.
In addition, a user can give multiple devices access to their Edge account. Although a token is saved on a specific device, users are not limited to just that device. Users can share their 2FA token with other devices by scanning a QR code or typing in an authentication code. Sharing the 2FA token gives access to multiple devices while still limiting access to only those devices authorized by the user.
To setup two-factor authentication on your Edge wallet, head over to the settings and unlock your account settings by typing in your password. Tap on ‘Setup 2 Factor’ from the Account menu.
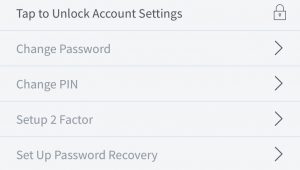
This will take you to the 2FA setup page where you can tap on ‘Enable’, and that’s it! Painless.
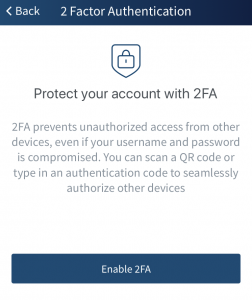
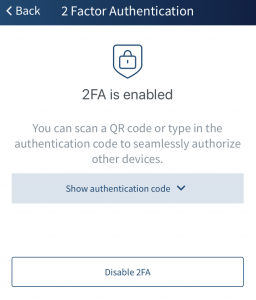
Safety, easy set up, and synchronization across multiple devices sets the Edge Wallet apart from other forms of 2FA to ensure your funds have that extra level of security needed for members of the burgeoning digital world.